How to disable Microsoft 365 Copilot Chat

Microsoft includes Microsoft 365 Copilot Chat in their business and enterprise Office365 services. If your organisation is not ready for this AI service, here’s how to disable it for now.

Microsoft includes Microsoft 365 Copilot Chat in their business and enterprise Office365 services. If your organisation is not ready for this AI service, here’s how to disable it for now.

If the parcel shell falls off in F-type Coupe here’s the fix.

Demos of the FITCAMX integrated dashcam for Jaguar F-Type.

How to upgrade the factory original speakers in a MY2016 Jaguar F-Type.
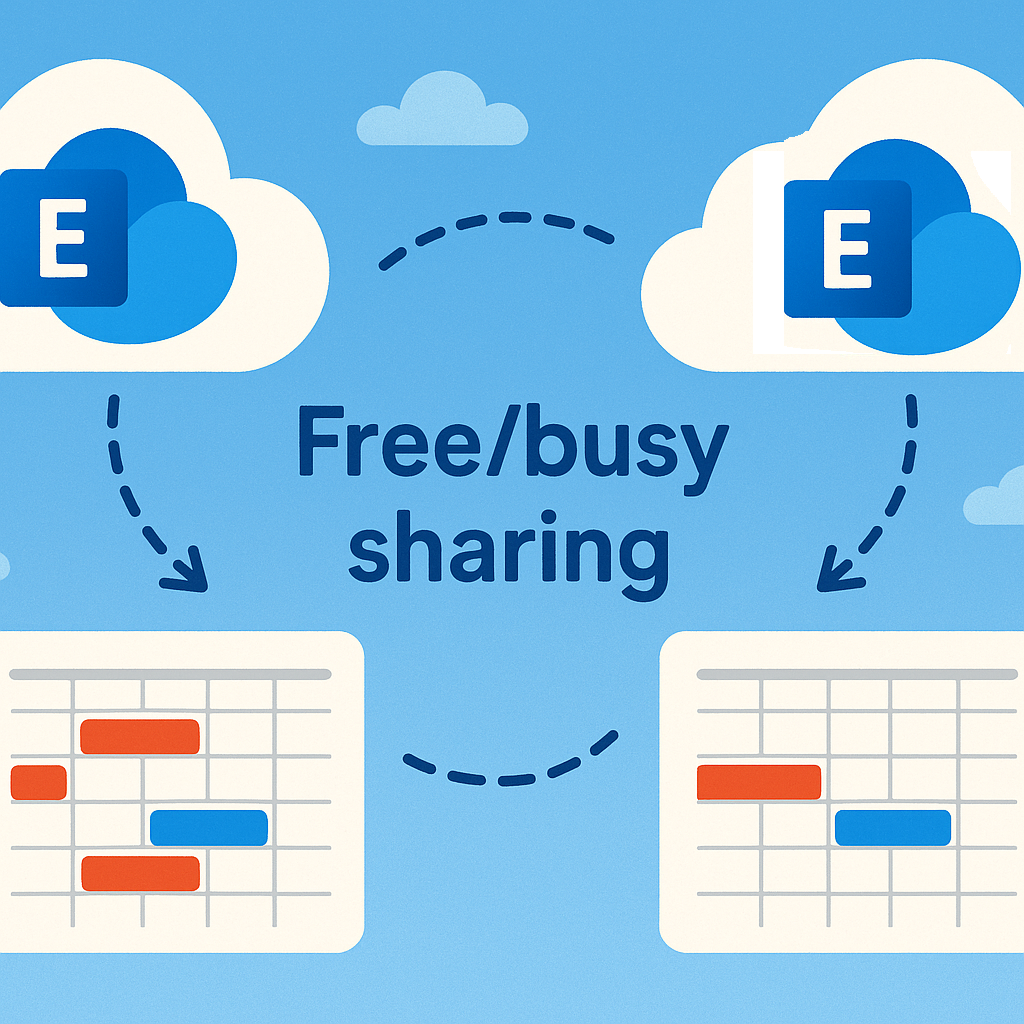
Scheduling meetings is tricky when people are split across different companies and you can’t tell when the other side are available. If both companies are using Microsoft Exchange Online mail, you can choose to share calendar availability. The Microsoft guidance didn’t work for me when one of the organisations was a more complicated Exchange Hybrid deployment. Here’s how to fix error message: “The recipient’s server could not be determined. Contact your administrator”

How to Install an aftermarket Apple CarPlay/Android Auto System in a Jaguar F-Type Without Losing Your Sanity (Mostly)
So, you’ve got yourself a Jaguar F-Type—a sleek, growling beast that makes heads turn at every traffic light. Congratulations! But wait, what’s this? The infotainment system looks like it was plucked straight out of the early 2010s? And you’re weaving between lanes trying to reroute on your phone while driving. Fear not, for there’s a solution: installing an aftermarket Wireless Apple CarPlay and Android Auto Interface.
Buckle up, because this is a story of ambition, frustration, and—if you’re lucky—triumph.
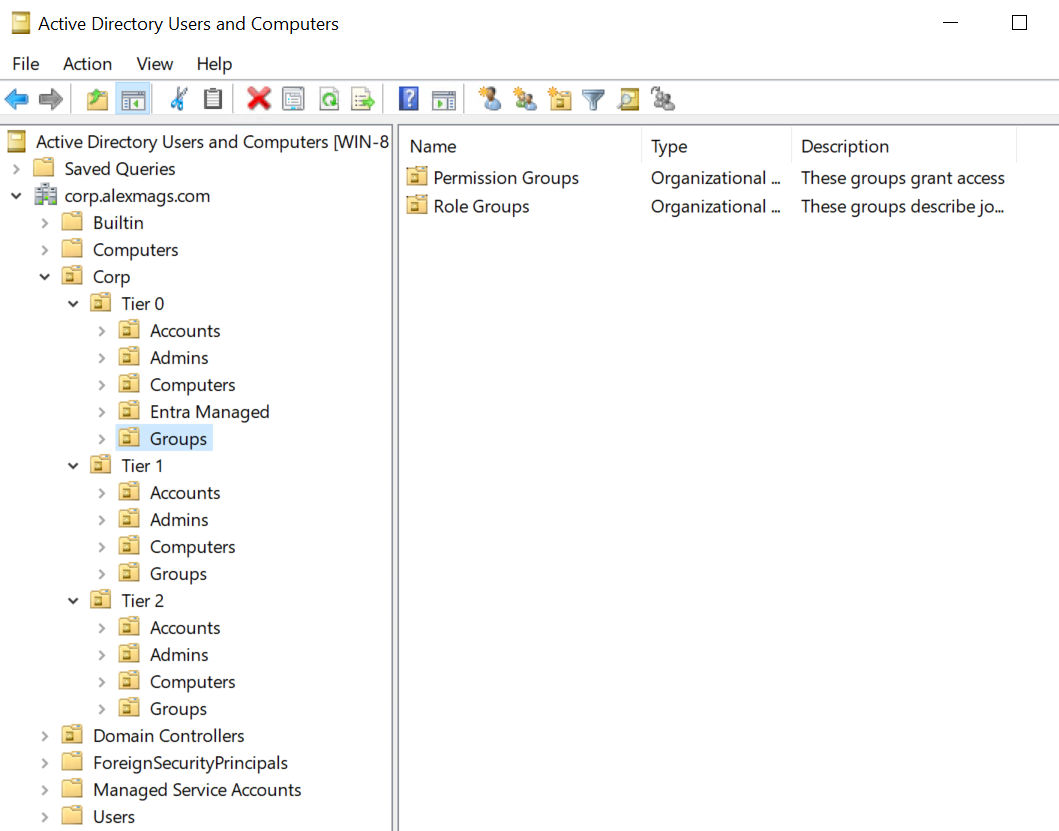
The Active Directory Tiered Admin Model is a way to organise AD users and groups with very clear boundaries between standard user accounts and their permission groups, server and application administrative accounts and groups, and domain wide access accounts and groups. Creating and enforcing these boundaries hinders privilege escallation from desktop/user level access to domain compromise. Here’s some automation to set it up.
Was your M365 tenant configured securely when it was deployed? Is it still configured securely now? Update on state of SaaS security posture management (SSPM) post from 2022. This time looking at community projects too.
Sign-in to Mimecast can either be “service provider initiated” (where you sign-in via mimecast’s web portal), or “idenity provider initiated” (where you sign-in via Entra myapps.microsoft.com portal). But why not both! This post shows how to enable both at once.
 “Create a picture in the style of a pixar movie of a friendly badger, working in an office IT department, using encryption to secure Microsoft Active Directory” - bing chat
“Create a picture in the style of a pixar movie of a friendly badger, working in an office IT department, using encryption to secure Microsoft Active Directory” - bing chat
This post describes how to keep user passwords transmitted in LDAP authentication requests safe. Lightweight Directory Access Protocol (LDAP) is an open standard for directories. It underpins Microsoft Active Directory Domain Services (ADDS). Applications need to check in with a central directory to authenticate user sign-ins. Other authentication protocols oAuth,SAML,Kerberos, even NTLM are prefered but still, even today, you’ll need to accomodate self-hosted business applicaitons that only support LDAP for authenticaiton. In my experience these are often JAVA developed apps or apps hosted on Linux. This post has some PowerShell generate encryption certificates (private and public keys) to enable SSL encrypted LDAPS communication with domain controllers.