Checking SaaS security configuration (SSPM)
Was your SaaS software configured securely when it was deployed? Is it still configured securely now?
This article discusses the risk to your data of misconfigured/unhardened SaaS software and the emerging products to automate security checking of SaaS.
The risk
Internet hosted software services have lots of security configuration options. It’s your responsibility to review these and make configuration choices. Your data could be exposed over the public internet if your software is misconfigured.
Keeping SaaS software configured safely is hard
Instead of self-hosting business applications on their own Windows and Linux servers, companies are increasingly using internet hosted software from application service providers. This is known as Software as a Service (SaaS). Two of the most well-known examples of this are the email, calendaring and productivity solutions Microsoft 365 and Google Workspace. The use of SaaS of self-hosted software is growing. Your HR, payroll and Finance systems might also be delivered as internet hosted SaaS also? The source code to your in-house software may be stored in online development services such as Azure DevOps or Github. Compared to systems within your own perimeter firewall, misconfiguration of internet facing software can be discovered and exploited by external actors with less effort. When some of our most sensitive information is stored in SaaS, how to manage the risk of security hardening settings being missed or undone?
Adaptive Shield (a SaaS security product vendor) commissioned The Cloud Security Alliance (CSA) to run a survey to better understand the use of SaaS applications, timeline and tools for SaaS security assessments, a timeframe for misconfiguration detection and remediation, and awareness of security tools for SaaS applications. The findings were:
-
SaaS misconfigurations are leading to security incidents
-
The leading causes of SaaS misconfigurations are lack of visibility and too many departments with access
“Forty percent of organizations report that departments with security access to SaaS apps are business departments (e.g., legal, marketing, sales) that are focused on performing job-related tasks.”
- Investment in business-critical SaaS applications is outpacing SaaS security tools and staff
“Over the past year, 81% of organizations have increased their investment in business-critical SaaS applications, but fewer organizations report increasing their investment in security tools (73%) and staff (55%) for SaaS security. This change means there is an increasing burden on the existing security teams to monitor SaaS security”
- Manually detecting and remediating SaaS misconfigurations is leaving organizations exposed
“When organizations manually monitor and remediate their SaaS security settings, it is taxing to the security teams and leaves the organization vulnerable. Nearly half (46%) can only check monthly or less frequently, and another 5% don’t check at all.”
Overall, the recommendation of this paper was to use automation to detect and remediate SaaS misconfigurations, so security teams can detect and respond more quickly.
The automatic auditing and policing of application hosting environments is a solved problem. AWS and Azure have policy engines for authoring configuration rules in audit only or enforce modes. There are also mature third-party Cloud Security Posture Management (CSPM) products, such as argos-security.io and turbot.com) to check and alert on misconfiguration of Infrastructure (IaaS) and platform services (PaaS). Unfortunately, these products don’t yet accommodate checking SaaS software configuration.
Microsoft 365 has no built-in policy engine for customers to build rules and enforce configuration. Microsoft Secure Score provides high level guidance for improving security posture (hardening). Microsoft 365 Defender Configuration Analyser provides more detailed guidance around configuring this part of M365.
Buy a solution or build one?
It’s possible to “roll your own” SaaS configuration checks. Testing frameworks, such as pester.io or inspec.io, can be used to build a barrage of SaaS configuration checks. CI/CD tools, as used by developers to test applications, can be reused to schedule the SaaS configuration checks and report any test failures. Exporting/backing up SaaS configuration and programatically comparing to a previous export/baseline is useful to identity changes/configuration drift. See talk slides here. But, in-house, scripted solutions require regular maintenance to keep in step with the rapid feature release cycles of SaaS software. “Buy rather than build” would be my advice as the SaaS Security Posture Management (SSPM) products on the market mature.
My suggestions
-
Discover which SaaS software is used in your organisation. Your identity services team will know software that is integrated with your identity providers for single sign-on (SSO). M365 E5 customers can use the Cloud App Discovery part of Microsoft Defender for Cloud Apps to discover and risk score cloud apps based on telemetry from desktops or by ingesting proxy logs, this will include the unsanctioned apps (shadow IT) used by your organisation. If you have Defender for Endpoint you could explore that dataset for file uploads to cloud apps to understand which cloud apps are used with your files.
-
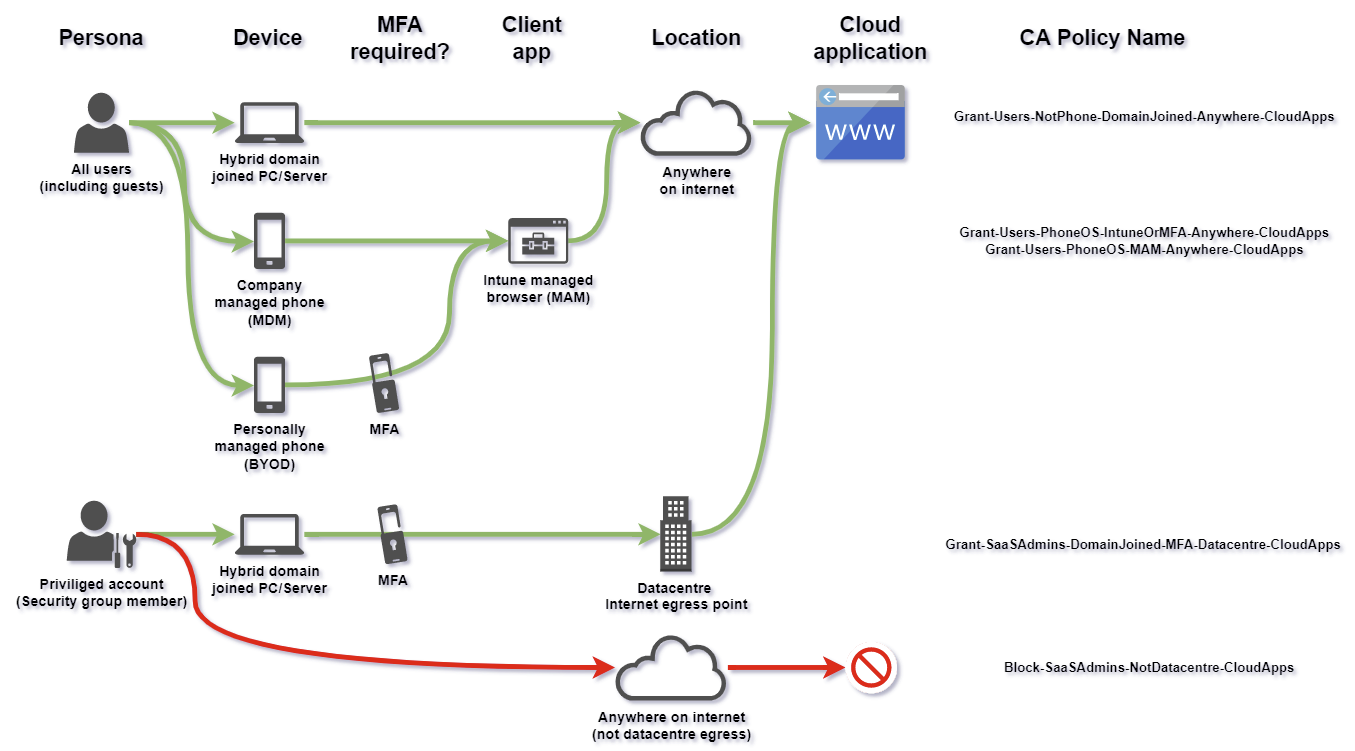
Ensure staff and administrators use company managed identities, with strong authentication (not only ID+password), to login to SaaS software. Assuming some credentials will get phished, require multifactor authentication and/or the use of a company managed device to login. Companies using ADFS and Azure AD, move SaaS authentication from ADFS to Azure AD to benefit from Conditional Access policies. Remove all local accounts within the SaaS software and replace with SAML/oAuth federation to your company identity service (for example Azure AD) to inherit your strong authentication services. See CA policy example diagram below. If you can’t disable built-in administration accounts, put them beyond use with an extremely complex password stored in a vault, and audit use of local admin accounts in SaaS. A01 Broken Access Control - OWASP Top 10:2021
-
Identify a SSPM product to continuously audit the SaaS software security controls that are important to your organisation. Enforce SaaS software configuration policies such as: No local accounts, MFA enabled, legacy protocols such as POP3/IMAP are disabled for mailbox access etc.. Integrate with your incident management service to automatically raise tickets for investigation & resolution. A05 Security Misconfiguration - OWASP Top 10:2021
-
Automatically collect and analyse administrative activity logs from SaaS software where you can (SIEM integration is uncommon for SaaS software.) Detect and respond to logins using local (backdoor) accounts bypassing the company identity service. Detect and respond to unusual activity such as the creation of local accounts or changes to administrative role membership. A09 Security Logging and Monitoring Failures - OWASP Top 10:2021
The report by CSA
2022 SaaS Security Survey Report.pdf
Example authentication flow for SaaS
This example of Azure AD Conditional Access ensures login to SaaS requires either a company machine or, in the case of BYOD phones, MFA. This hinders the use of comprimised / phished credentials.
The end
