Active Directory Tiered Administration Model
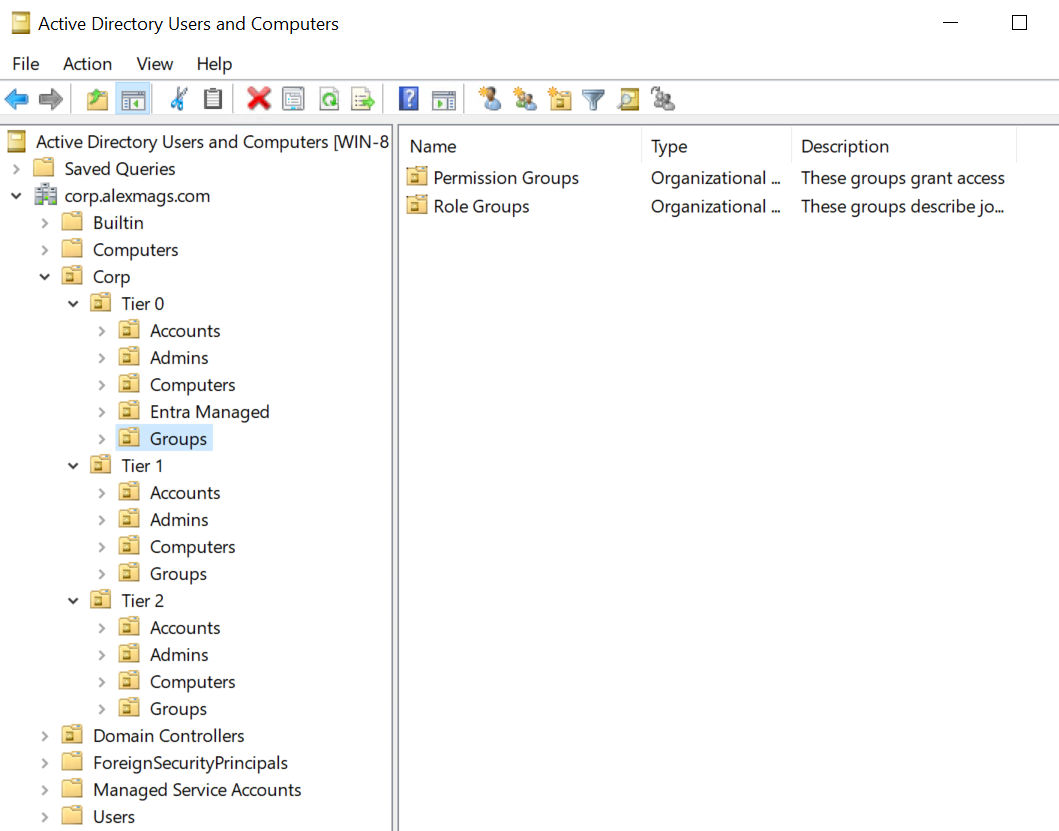
The Active Directory Tiered Admin Model is a way to organise AD users and groups with very clear boundaries between standard user accounts and their permission groups, server and application administrative accounts and groups, and domain wide access accounts and groups. Creating and enforcing these boundaries hinders privilege escallation from desktop/user level access to domain compromise. Here’s some automation to set it up.

 “Create a picture in the style of a pixar movie of a friendly badger, working in an office IT department, using encryption to secure Microsoft Active Directory” - bing chat
“Create a picture in the style of a pixar movie of a friendly badger, working in an office IT department, using encryption to secure Microsoft Active Directory” - bing chat