How to Disable NetBIOS and LLMNR

Hey defenders! Hackers and pentesters hate it when you disable the old NetBIOS network service. They love to respond to NetBIOS requests from PCs on your company LAN so they can impersonate your servers and steal some credentials. Here’s how to disable the old NetBIOS service so as not to give hackers and pentesters an easy ride.
These captured credentials give attackers a foothold into your environment to hack further. NetBIOS is installed by default to help find other machines within a LAN/subnet and maybe it helps connect machines on your home LAN. But the days when everything was on just one LAN/subnet in a company are long gone. Instead, in networks of more than one subnet, DNS is used by clients to find servers.
The Centre Of Internet Security (CIS) baseline recommendation for Windows clients is to disable multicast name resolution.
18.5.4.1 (L1) Ensure ‘Turn off multicast name resolution’ is set to ‘Enabled’ (Scored) To completely mitigate local name resolution poisoning, in addition to this setting, the properties of each installed NIC should also be set to Disable NetBIOS over TCP/IP (on the WINS tab in the NIC properties). Unfortunately, there is no global setting to achieve this that automatically applies to all NICs - it is a per-NIC setting that varies with different NIC hardware installations.
Disabling Link Layer Multicast Name Resolution (LLMNR)
Via Group policy use the setting:
Computer Configuration\Policies\Administrative Templates\Network\DNS Client\Turn off multicast name resolution
How to check if NetBIOS is enabled
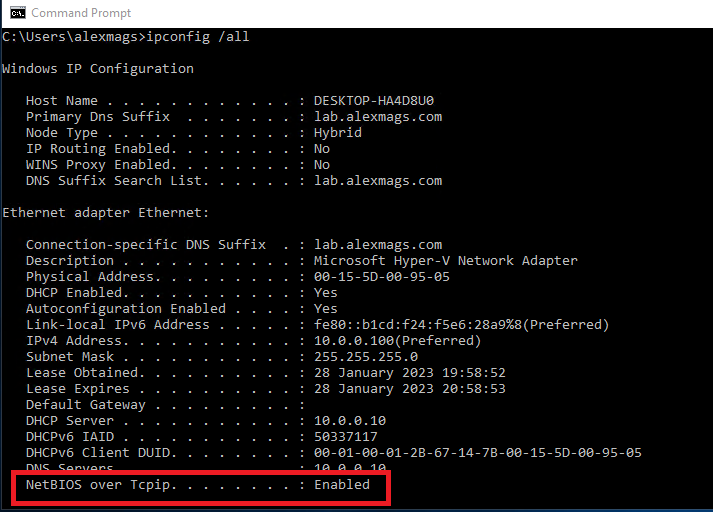
Run the command ipconfig /all and check the NetBIOS over Tcpip value.
How to disable NetBIOS via Group Policy / Intune
There is a policy setting to disable LLMNR, but there is no policy setting to disable NetBIOS. Its baffling….
How to disable NetBIOS (manually)
- Click Start, point to Settings, and then click Network Connections.
- Right-click the local area connection that you want to be statically configured, and then click Properties.
- Click Internet Protocol (TCP/IP) > Properties > Advanced, and then click the WINS tab.
- Click Disable NetBIOS over TCP/IP.
How to disable NetBIOS (automatically)
Check under registry key HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\NetBT\Parameters\Interfaces, find the GUID(s) for each network interface with NetbiosOptions set to 0 and set them to 2. This is the equivalent of setting NetBIOS disabled in the Network Adapter settings GUI (WINS tab). There’s a few ways to programmatically turn off NetBIOS on each NIC. Use vbScript, WMIC or PowerShell. Here’s a PowerShell command for it. The command can be deployed with a group policy shutdown script, or wrapped in a package and deployed with your software deployment tooling: Apply the change with value 2
# disable NetBIOS over TCP/IP (legacy protocol not required)
Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Services\netbt\Parameters\interfaces\tcpip_*' -name NetBiosOptions -value 2 -Verbose`Revert the change back to value 0
# Re-enable NetBIOS over TCP/IP on new adapter
Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Services\netbt\Parameters\interfaces\tcpip_*' -name NetBiosOptions -value 0 -Verbose`Here’s another PowerShell script using Windows Management Instrumentation (WMI). It enumerates all the network interfaces that are IP enabled and sets the NIC’s NetBIOS property to disabled.
# disable NetBIOS over TCP/IP (legacy protocol not required)
$NETBIOS_DISABLED=2
$NETBIOS_DISABLED=0
Get-WmiObject Win32_NetworkAdapterConfiguration -filter "ipenabled = 'true'" | ForEach-Object { $_.SetTcpipNetbios($NETBIOS_DISABLED)}How to disable NetBIOS (via DHCP)
This method is effective for clients on a corporate LAN, but laptops will revert back to NetBIOS broadcasts when they’re on other networks.
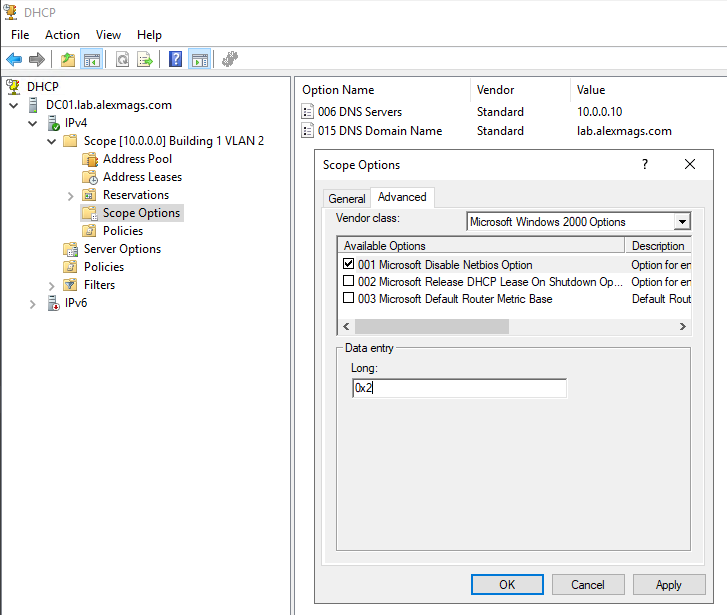
Find the DHCP scope option -> advanced -> Microsoft WIndows 2000 options -> 001 Microsoft Disable NetBIOS option = 0x2
Rather than setting this per-scope, consider setting this as a server option so it applies for all scopes. See Microsoft docs link at the end of this article.
How to disable NetBIOS (via Cisco and other DHCP)
This article describes DHCP Option 43. In summary, option 43 must be set with the following bytes 01 04 00 00 00 02.
ip dhcp pool Building1VLAN2
....
option 43 hex 0104.0000.0002So which method?
Disable NetBIOS by a change on clients, or disable NetBIOS by a change in DHCP? Why not both?
Login scripts when NetBIOS is disabled
The Policy Setting may be required if clients are in a different domain to domain controllers (cross forest) and DNS suffixes are not configured. Software\Policies\Microsoft\Windows\System\Allow-LogonScript-NetbiosDisabled
What is NetBIOS doing?
NetBIOS names are short hostnames like FileServer01 DNS names are longer and include the context of domain name. For example fileserver01.companyname.com
We’re used to using longer DNS names to connect to sites on the public internet. Often a web server on the internet is presented as called www and then the company’s domain name afterwards. But within a company, IT admins, desktop support and staff often revert to the shorter NetBIOS style names for less typing. This means Windows has to do more work to figure out which Filesevrer01 on the whole of the internet you mean.
When clients want to connect to a machine using a DNS name (fileserver01.companyname.com), clients send a name resolution request to DNS servers to resolve the fully qualified domain name (FQDN) to an IP address. So far so good.
When clients want to connect to a machine using short NetBIOS style names (FileServer01), Windows shouts across the LAN “HEY! IS ANYONE FILESERVER01?!”
Usually the server is on some other subnet in a datacentre, so no machines on the local LAN respond.
In parallel, Windows starts guessing what the fully qualified domain name for fileserver01 might be, by appending domain names in your organisation, starting with “primary DNS suffix” so see if by appending a domain name to the end of the NetBIOS name you get a hit in DNS. In a small organisation you likely have only one DNS domain name to check. In a larger organisation with multiple domains you might have several DNS domain names to hunt through in your DNS suffix search list. Tip: Run ipconfig /all and check the Primary DNS suffix and the DNS suffix search list there.
With a bit of luck, the somewhat vague NetBIOS name gets been resolved to a specific DNS name after the automated guess work.
The problem is that broadcast across the LAN “HEY! IS ANYONE FILESERVER01?!”. Hackers and pentesters like to fire up their network traffic capture tools and capture these broadcasts. They also have tools like Responder (included in Kali Linux) to automatically respond to these broadcasts with “SURE, I’M FILESERVER01, HONEST! SEND YOUR CREDENTIALS TO LOGIN!”
References:
- MITRE Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay
- Example using Responder in Kali Linux
- Microsoft docs disabling NetBIOS via DHCP
- Black Hills blog disabling LLMNR
- PowerShell and Intune to disable NetBIOS
- Powershell to disable NetBIOS over TCP/IP My post from 2015. Been turning off NetBIOS for YEARS! You can too!
