Exchange Online Migration gotchas

Exchange Online migration is a complicated project in a large organisation. So complicated that some organisations haven’t completed this yet. There’s many technical integrations and operational processes with this service. Here’s a post about technical and operational problems that can occur when migrating email to Exchange Online. What has tripped you up in an Exchange migration? Let me know what I’ve missed!
Why migrate email services to Exchange Online?
This project can be expensive in time and effort so it’s important to identify the value to the company of doing this work. What are the benefits you expect to gain from this project? How to measure success? Note them down and make sure your project team hit them all before closing out the project:
Goal: A more reliable email service
Gather some stats regarding your on-premises email service outages in the last year. After migration to Exchange Online you should enjoy a more reliable service (assuming you have resilient internet services from the Office) https://docs.microsoft.com/en-us/office365/servicedescriptions/office-365-platform-service-description/service-health-and-continuity
Goal: Communications independent of datacentres
Coordinating datacentre recovery is hampered if your communications systems are also down. If a goal is to continue to communicate in the case a datacentre outage, ensure you don’t build any datacentre dependences into your mail flow.
Goal: Reduce operational overheads (Exchange Server maintenance)
After migration to Exchange Online you’ll be able to decommission the majority of your Exchange Server infrastructure (servers and storage). There will be less infrastructure to patch, update, monitor. Ensure decommissioning redundant infrastructure is part of your migration plan. You’ll still need engineers to manage the Exchange Online tenant and it’s mailboxes.
Goal: Improved email experience when remote
Connecting to the corporate datacentres will no longer be required to access email (VPN). Only an internet connection is required. If you used a
Goal: Decommission alternative mobile email service
If you ran Blackberry Enterprise Server (BES) or Good for Enterprise to secure email stored on mobile devices, with the correct Intune Mobile App Management policies.
Goal: Decommission traditional email filtering smart host
If you run a smart host service to filter inbound email, you have an opportunity to switch to Exchange Online Protection aka Defender for 365. This will require your security team to learn how to operate a different product. Some processes will need to be updated.
Goal: New Office365 features
Look into components of the Microsoft 365 suite that require Exchange Online and can be enabled. Microsoft Viva Insights helps you manage your inbox and scheduling. Microsoft To Do (a lightweight task tracker) integrates with Outlook tasks.
Technical pre-requisites
There’s some technical groundwork to do before migrating the first mailbox to a new production ready Exchange Online service.
Hybrid Identity Service
Much like Exchange Server is tightly integrated with Active Directory Domain Services, Exchange Online is tightly integrated with Azure AD. You’ll will need:
- On-prem AD objects (users, security groups, distribution lists, contacts) synced to Azure AD.
- Hybrid domain join (useful to identify company managed PCs compared to personally owned unmanaged PCs) Microsoft docs:Hybrid domain join
- Custom AD account properties synced
Not all AD account properties have an Azure AD equivalent (the AD division property for example). Some are not synced by default. If you need these in Azure AD for reporting, retention policies, dynamic distribution groups or dynamic legal signatures consider mapping these to an Azure AD Custom Security Attribute or additional attribute in Azure AD Connect. Tip: Mapping AD distinguished name to an Azure AD custom attribute is handy if AD OU path is meaningful in your organisation.
Privileged Access to Exchange Online
It’s tempting to grant your existing AD accounts access to Exchange Online for administration. Instead create dedicated Azure AD cloud accounts for privileged access to Office365. Microsoft’s current security guidance is to use separate privileged accounts in AAD/Office365 compared on on-premises. This is to avoid a compromise of on-prem AD leading to compromise of Office365 also. Compartmentalise your on-prem and cloud privileged accounts. Microsoft docs: Enterprise Access Model
Conditional Access
Your on-prem email service is secured behind a perimeter firewall where only machines with access to the client VPN service could access mail. Exchange Online, on the other hand, is presented on the public internet. “Identity is the new firewall”. Blocking sign-in from unexpected devices and applications is essential. Map out all the combinations of identities/personas + devices + client applications + internet locations that will be permitted to access Office365. Document your CA policies well. This will get complicated as more exceptions appear. Consider versioning CA policies as code. I find this method of visualising CA policies us useful in conversations about authentication. Monitor for unauthorised changes to Conditional Access policies in AAD audit logs. To reduce the risk of unauthorised changes, require approval for the Conditional Access Administrator role in Azure AD PIM.
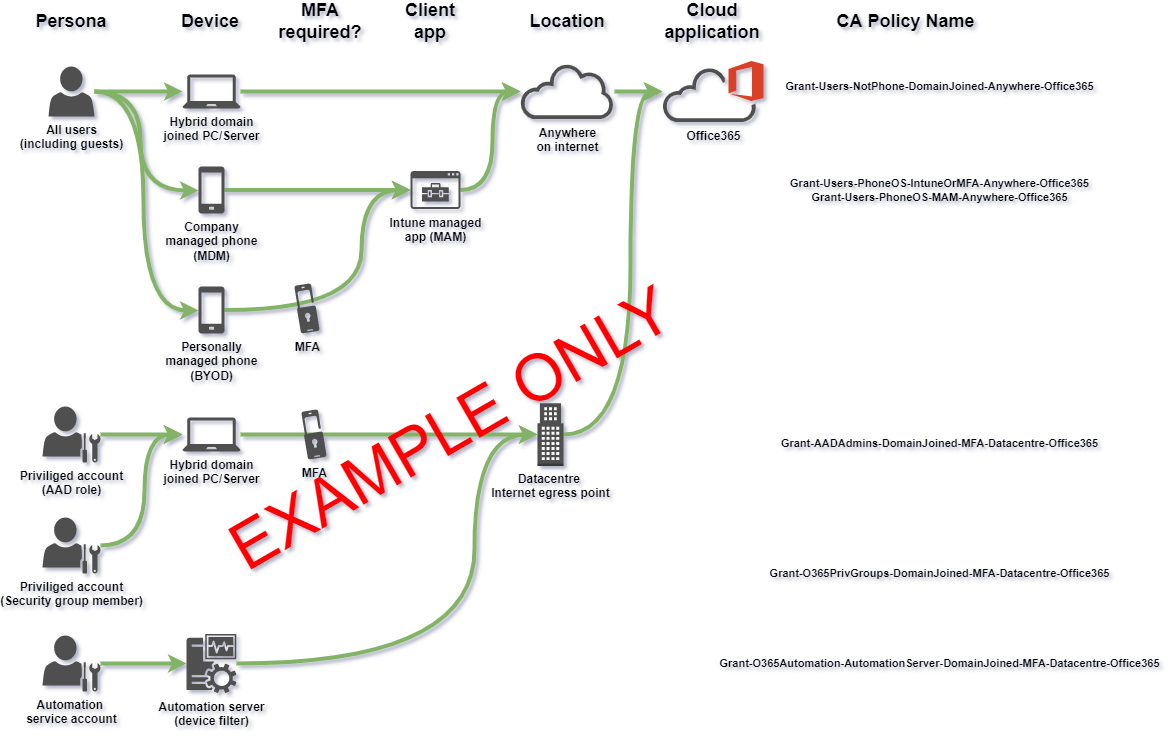 Above is just an example of documenting CA policies visually. Your CA policies will be different based on your own environment and security requirements (there are more exceptions such as shared user accounts, meeting room equipment etc..)
Above is just an example of documenting CA policies visually. Your CA policies will be different based on your own environment and security requirements (there are more exceptions such as shared user accounts, meeting room equipment etc..)
Resources:
- Microsoft docs: Conditional access filtering
- Microsoft docs: Emergency access break glass account
- CA policy automation options
- CA policy automation and naming convention
Privileged account management
If you have an existing service for managing access to privileged accounts in Active Directory, check if this is also compatible with Azure AD. Alternatively deploy Azure Privileged Identity Management (PIM) for temporary access to privileged Azure AD roles such as Exchange Administrator. You can also temporarily escalate to membership of privileged Azure AD groups. Microsoft docs:AAD PIM & Priviliged groups
Exposing Exchange Server on public internet
With Exchange Hybrid you must publish the Autodiscover service from your internal servers to the public internet. Exchange servers are typically on the internal network (not in a DMZ). This is a risk that must be managed. Microsoft docs:autodiscover pre-requisitie
Azure MFA & Microsoft Authenticator mobile app
You will need MFA for:
- Privileged accounts
- Sign-in from unmanaged devices (eg BYOD phones)
- Intune device enrolment (device becomes more trusted)
- Additional security controls in Azure AD Identity Protection
- Ensure staff enrol for MFA from a trusted/managed device Enroling in MFA is somewhat fiddly and will require good user guides and videos. Also plan for MFA enrolment/reset for staff that don’t travel with a managed device (perhaps iPad only.) When staff are enrolled in Azure MFA you have an opportunity to decommission other MFA services you might have (such as a client VPN MFA service).
Azure AD group based licensing and mailbox lifecycle management
Manually assigning licences per-mailbox doesn’t scale well. Instead you’ll configure AD group based licensing. Every account with the Exchange Online component enabled in a M365 licence assignment will automatically get an Exchange Online mailbox when an on-prem Exchange Server mailbox doesn’t exist. You may find that test accounts, automation accounts, shared accounts are automatically provisioned an Exchange Online mailbox. Adjust group based licensing to better control which accounts receive an Exchange Online licence and mailbox.
Also, staff accounts are temporarily disabled for various reasons. If you revoke Exchange Online licence for disabled accounts their mailbox will become inactive and unusable. This is different behaviour compared to Exchange Server where the mailbox associated with a disabled account continued working. Map out the user account lifecycle, including “disabled but we still want to monitor the mailbox for a while”. You’ll need to purchase licences for mailboxes in the “dormant but active because reasons” state (Exchange Online P2).
Anyone who’s data will not be stored in the default region must have multi-geo licence assigned.
Inbound mail flow (MX record)
There is a decision point for when to repoint inbound email routing MX record to Exchange Online. Include this in the migration plan. This is necessary to remove dependency on datacentre for email routing.
Outbound mail flow (mandatory TLS encryption with 3rd parties)
Your organisation may require TLS encryption (mail server to mail server communications) when exchanging emails with some organisations. Prepare transport rules equivalent to those you have on-prem to make TLS encryption mandatory rather than opportunistic.
Free/busy sharing with other email organisations
You may have partner organisations with which you enable free/busy information sharing for easier meeting scheduling. Include this is your plan.
Exchange Online tenant configuration
This is a big topic. Decide on a tenant level configuration for Exchange Online. Document this as follows to create a record of customisation:
| The setting name | Microsoft default value | Our value | What it does | Justification for change (why we messed with it) |
|---|---|---|---|---|
| AuditDisabled | False | False | Disables auditing at tenant level | No change. Auditing must be enabled |
| AllowPlusAddressInRecipients | True | False | Disposable subaddressing as defined in RFC 5233. | Decision by XYZ, this is disabled to simplify eDiscovery investigations. |
| etc…. |
Expect the configuration of Exchange Online to change over time due to:
- Troubleshooting by IT admins
- Troubleblasting (similar to troubleshooting but doing more harm than good by changing everything!)
- Accidential changes (human error)
- Unauthorised changes (tampering)
- Microsoft introducing new features with new configurable settings
Detect these changes by automatically and continuously testing Exchange Online tenant config. Regularly compare your Office365 tenant config to security best practice configuration using a security posture management (SPM) service such as Secure Score. Establish security posture reviews as new recurring process (for example, monthly). On a weekly basis, triage the regular Exchange Online service change announcements from Microsoft. This will ensure your on top of new Exchange Online features before Microsoft automatically updates your tenant.
References:
- Microsoft docs:Exchange Online config settings
- Microsoft docs:Exchange Online recommended policies
- CIS baseline for Office 365
Exchange Online mailbox configuration
Ensure there is a standard configuration for Exchange Online mailboxes. Ensure new mailboxes automatically receive this configuration via a default mailbox plan. Plan to manage exceptions where some mailboxes may need different features enabled. Plan to regularly and automatically compare mailbox configuration to standard to detect misconfiguration and automatically remediate. Expect mailboxes migrated from on-prem, and mailboxes restored from backups, to be misconfigured. Be able to detect and remediate these very quickly.
Exchange Online Protection / Defender for 365 configuration
This solution is designed to block malware, phishing and spam. Allow time for your IT Security admins to configure this service compared to their previous smart host system.
Data residency - Preferred Data Location (PDL)
Office365 will store data in the default region which is based on the company used to purchase the subscription or Enterprise Agreement. If you have data residency requirements, to store mail in different regions on a per-user basis, you must manage the Preferred Data Location attribute and also purchase and assign additional ‘multi-geo’ licences for anyone who’s data will not be stored in the default region. PDL value can be set on AD user account and synced by Azure AD Connect. Or derived some other way by Azure AD Connect, perhaps on OU or mail domain. Microsoft docs: managing preferreddatalocation. Consider making PDL value a pre-requisite for Office365 licence assignment to ensure data is never placed in wrong (default) location.
Mailbox backup for recovery
The service used to backup and restore on-prem mailboxes may not be optimised for Office365. Ensure a mailbox backup solution is in place and tested before data migration. Decide on naming convention and lifecycle management for restored mailboxes and ensure they’re captured in mail retention and deletion processes. Random unmanaged restored mailboxes popping up is a challenge for reporting on eDiscovery retention coverage.
Email data retention and eDiscovery
On-prem, email was shipped to a storage service for long term retention (journalling). An eDiscovery service was integrated with the storage service for search, export and processing (filtering, redactions etc.) A decision is required to continue with the existing on-prem journal service, or switch to Office365 in place retention. The team responsible for performing eDiscovery investigations will be greatly impacted by this decision. Consider that other Office365 services may require data retention also (Teams chat, OneDrive & SharePoint files). Role based access control must be configured to accommodate all the personas using the Office 365 Compliance Centre / Microsoft Purview.
Legacy mailbox protocols
If your email team are on top of their game, unused mailbox protocols (POP3,IMAP,ActiveSync) are already disabled. Since your moving mailboxes to public internet, take this opportunity to ensure these protocols are disabled on every mailbox before it’s moved to Exchange Online. Ensure new mailboxes created on Exchange Online have legacy protocols disabled.
Shared mailboxes and mailbox and calendar delegation
Plan to identify where there is shared access or delegated access to mailboxes and calendars. Use this to inform mailbox migration batches so that people sharing access to a mailbox are migrated together. Microsoft docs: Exchange hybrid and delegate mailbox permissions
Outlook Notes
Someone in the organisation will use the sticky notes like feature in Outlook. Deletion rules in Office365 retention policies will delete these if they were created long ago. Be prepare to recover them from backup and export these notes somewhere else (like Microsoft To Do).
Inbound email anti spoofing (SPF,DKIM,DMARK)
There is a limit of 10 DNS lookups in the Sender Policy Framework (SPF) mechanism designed to hinder spoofing. You’ll need to add Exchange Online as an expected sender. If you already have 10 lookups for systems that send email on your behalf (marketing, CRM systems etc..) you’ll need to identify a service this is no longer required. Consider reconfiguring sending applications to sendAs a subdomain such as no-reply@**events.**companyname.com.
Phishing simulation services
If you have a third-party phishing simulation/education service you must setup an Advanced delivery policy. Adding the sender to anti-spoofing exception list will not permit phishing emails to pass.
Desktop Operating System patching and software rollouts
If you depend on an on-demand Remote Access VPN connection for operating system updates and software rollouts, your deployment success will decrease after Exchange Online migration as staff will less frequently use the VPN service. When business applications and email are internet hosted (SaaS) services, there’s less incentive to connect to the Remote Access VPN service. Ensure your OS patching and software deployment services are effective for internet connected endpoints. If running Microsoft SCCM ensure this is fully up to date and review the Cloud Management Gateway feature and plan for internet-based clients.
Mobile device management (MDM)
With company email in Microsoft Outlook mobile app, it’s important to be able to keep mobile phone OS versions within Microsoft supported versions. The Outlook mobile apps for iOS and Android have minimum supported OS versions so expect to keep company managed phones at a minimum OS version. Get well practiced at OS deployments to phones.
Mobile application management (MAM)
Mobile Device Management (MDM) is only available for company managed phones. Mobile Application Management (MAM) protects company data on both Company and Personally managed phones (BYOD). A mobile application with a MAM policy assigned should be a requirement to sign-in to Office365 from phones (See Conditional Access policies above). Test that native mail apps, and alternative mobile email clients (GMail, BlueMail, Boxer, there’s loads!), are all blocked from Office365. MAM policy is the primary method for protecting company data within mobile apps. Microsoft docs: Intune MAM app protection 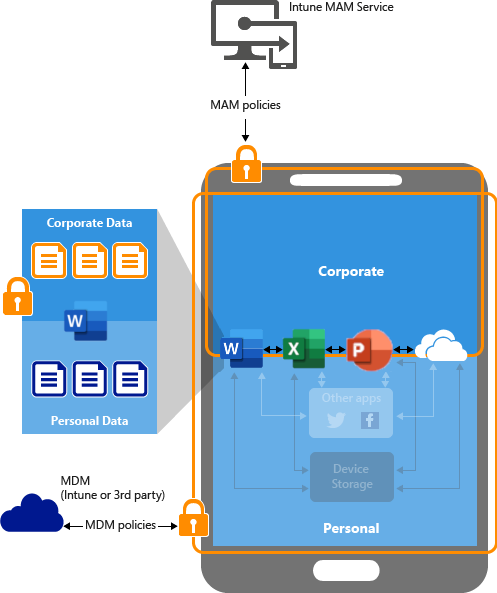
Licensing for shared mailboxes with retention policy
On-premises shared mailboxes were essentially free (though your storage team may have another view on that). Shared mailboxes are no longer free where in-place retention is required. In Exchange Online, if shared mailboxes require Office365 retention policies for eDiscovery you will require additional licences and a method to identify the shared mailboxes and automatically apply at least Exchange Online P2 “user” licence. Your Exchange Online backup service may also change for these additional licenced “users”.
Licensing for user mailboxes where owner has left but mailbox is still active because “reasons”
In Exchange on-premises the mailbox of a leaver remains active until it’s decommissioned. Again, these mailboxes didn’t require additional licences. In Exchange Online you’ll require a licence to keep the mailbox active. Be on the look out for “user mailboxes” where the user no longer exists but the mailbox is still required.
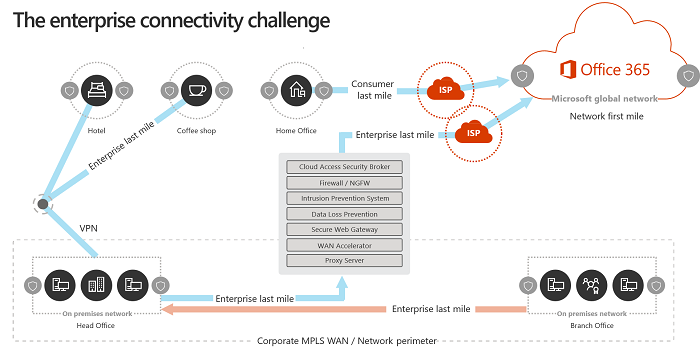
Office local area network (LAN) optimisation for Exchange Online
You office LAN is configured to get network connected clients to the datacentres. Plan to make network changes to optimise access to internet hosted Office365. This means local internet breakouts at each office and bypassing proxies and any in-line inspection/surveillance systems. Microsoft docs: Microsoft 365 network optimisation. On this topic, the OneDrive Sync Client reports telemetry about client internet access and can help you identify branch offices with less than optimal internet access Go to Service health in the Microsoft 365 admin center. Enterprise Agreement customers can request an Office365 Network Assessment engagement from their account team to take measurements from up to 5 office locations and generate a report of recommendations, reusing this tool.
Office LAN DNS resolution for Exchange Online (GeoDNS)
Exchange Online uses GeoDNS to find the nearest regional “Client Access Front End (CAFE)”. The DNS service should return the fully qualified domain name (FQDN) of the nearest global Exchange Online service. When on the office LAN, or connected to the company remote access VPN service, the company may have a central DNS service that always returns the Exchange Online service nearest to some central datacentre rather than relative to the client.
Test this by looking up the DNS address outlook.office365.com.
Command line: nslookup outlook.office365.com
The result will contain a three letter IATA airport code. Your result may be different when at home, when connected to the company VPN and when in the office. Plan for GeoDNS name resolution where each office location forwards internet DNS resolution requests direct to an internet hosted DNS resolution service rather than a central datacentre.
Remote Access VPN optimisation for Exchange Online
While clients are connected to corporate VPN, ensure connections to Exchange Online bypass the VPN and route direct to internet. This is known as Split Tunneling
Legal disclaimers and email signatures
The on-prem email routing servers may have had custom software installed to apply legal disclaimers and (branded) email signatures. Sometimes with complicated rules based on country/company/department etc. It’s not possible to add customisation software to Exchange Online tenant systems in this way. Plan to switch to an alternative system to manage legal disclaimers and email signatures.
Distribution Lists (on-prem vs cloud)
Plan to move email distribution lists from Active Directory to Azure AD. This requires (automated) export & delete from AD/Exchange and recreate in AzureAD/Exchange Online from export. Without this, users will loose the ability to manage distribution lists they own after migration to Exchange Online. Note that Office365 Groups (as used by Microsoft Teams) also act as email distribution lists.
Dynamic Distribution lists
Automatic distribution list membership based on department or location are common. Plan to migrate and managage Dynamic Distribution Lists in AzureAD\Exchange Online. Look into custom recipient filters.
Outbound email from business applications (SMTP relay)
Some on-prem applications will send email internally or externally via (sometimes anonymous) SMTP. Also some office equipment will send mail such as scan to PDF photocopiers. You options are:
- Reconfigure the application use use a service account with modern authentication to Exchange Online
- Reconfigure the application to use Graph API to send mail
- Leave an Exchange server on-prem for SMTP relay
- Deploy an alternative on-prem SMTP relay service to store and forward mails to Exchange Online
Business applications with mailbox integration
This is less common but some business applications will poll mailboxes to collect and process inbound emails. CRM software scraping inbound mail for contact with customers. Helpdesk systems scraping inbound email to generate tickets. Identify these and either leave these mailboxes on-prem or plan to move them to Exchange Online. Ideally these are the only on-prem mailboxes with POP3 or IMAP protocol still enabled.
Service health monitoring
Your Exchange Server health monitoring systems may not be able to monitor the health of Exchange Online. Your support teams will not receive notification of an email service outage before users call. To monitor email service from the point of view of users, detecting local problems with connectivity, you’ll need some user experience agent or some system monitoring using synthetic transactions. To monitor email service from Microsoft availability point of view you need something to watch the Microsoft 365 Service Health API
Mailbox forwarding
Mailbox forwarding isn’t carried over to Exchange Online when mailbox is moved. Identify mailboxes with mailbox forwarding settings before migration. Perhaps that account shouldn’t be forwarding to their personal Gmail account anyway ;-)
Outlook add-ins
With Office365, prepare to deploy Outlook add-ins centrally via the Microsoft 365 admin center, rather than traditional desktop software packaging and deployment. Some Outlook add-ins may need to be updated as part of mailbox migration to Exchange Online. The CIS benchmark for Microsoft 365 recommends disabling the ability for users to download and install random add-ins from the add-in market place so be ready to make these available via the Admin Centre when required.
Analysis of audit logs
To detect unauthorised or risky changes you will need to design auditing, log analysis and alerting to your Security Operations Centre (SOC). Microsoft Defender for Cloud Apps has an activity log analysis component with many built-in detections for risky activity. Microsoft have a cloud hosted SIEM called Sentinel and are authoring detections there. The following Microsoft 365 data sources are always free for all Microsoft Sentinel users:
- Azure Activity Logs
- Office 365 Audit Logs (all SharePoint activity and Exchange admin activity)
- Alerts from Microsoft Defender for Cloud, Microsoft 365 Defender, Microsoft Defender for Office 365, Microsoft Defender for Identity, Microsoft Defender for Endpoint, and Microsoft Defender for Cloud Apps.
Also, E5 licenced users have a grant of 5MB per-user per-day for M365 audit data. If you have an on-premesis SIEM for log analysis, check if it has a management pack to make send of Exchange Online or Office 365 unified audit log. If you need to store audit logs long term, you options are in-place retention or a 3rd party tool (Quest has one). If you have E5 licences you can configure M365 audit log retention from 90 days (default) to 1 year. If you purchase additional per-user add-on licence you can retain audit logs in M365 for 10 years. Microsoft docs: Audit log retention. Review which systems will consume the audit logs and what their integration capabilities are.
Operation pre-requisites
There’s some groundwork to ensure operational teams are prepared to run an Exchange Online email service.
Update new joiner process and automation to create new mailboxes on Exchange Online rather than Exchange Server
Often a central team is responsible for all the technical and procedural steps required on onboard a new member of staff. Often there is (Robotic Process) automation to ensure this process is completed consistency. Review the user account and mailbox management processes and update these to target Exchange Online rather than Exchange Server.
Email delivery troubleshooting
Email delivery troubleshooting is similar to on-prem using track and trace tool.
Emergency search and purge
Occasionally its necessary to search and purge emails from mailboxes across the organisation. For example if malware or a phishing link slipped though filters and was delivered to a distribution list. This requires a combination of Exchange Admin and Compliance Centre/Purview permissions. Plan to configure a custom RBAC role for least rights privilege to these permissions. When its required it’ll be an emergency so have this updated process documented and tested in advance.
Ensure service desk and IT support are onboarded early
Your support teams will need practice using and supporting the new email service. Onboard them early so they can help update user guides.
