Active Directory Tiered Administration Model
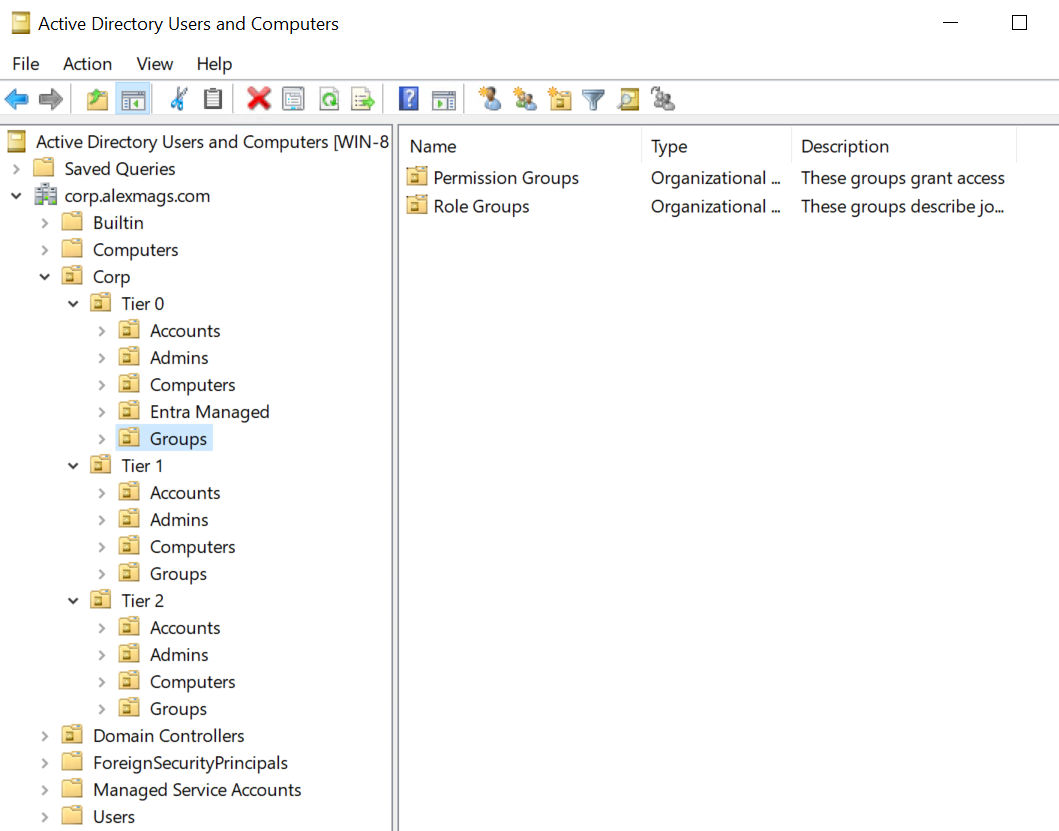
The Active Directory Tiered Admin Model is a way to organise AD users and groups with very clear boundaries between standard user accounts and their permission groups, server and application administrative accounts and groups, and domain wide access accounts and groups. Creating and enforcing these boundaries hinders privilege escallation from desktop/user level access to domain compromise. Here’s some automation to set it up.
Background reading:
- Microsoft describing Protecting Tier 0 the Modern Way
- Microsoft describing how to protect domain admins
- SpecterOps Tier zero table
- TrueSec describing their implementation to Tiered admin model
- Quest describing Tiered admin model
- Trimarc describing using restricted groups, via Group policy, to block higher tier accounts being used on lower tier machines
Here’s the code: https://github.com/alexmags/ADTiersOfJoy
The code:
- Creates Organisational Units (OUs) under a new root OU.
- Creates security groups for roles and permissions
- Nests permissions groups into role groups
- Delegates permissions to OUs
You then:
- link your existing Group Policy Objects (GPOs) to new OU structure
- Make GPOs to deny login to workstations and application servers with domain admin accounts (no cached domain admin creds on desktops)
- Update the domain join step of your desktop and server deployment automation. New service account for desktop deployment, not domain admin, with in role group to add desktops to T2 OU. New service account for server deployment, not domain admin, in role group to add servers to T1 OU
- Move over your users, groups, machines to the new OU structure following the Tiered Administration Model principles
