Mimecast authentication with Entra ID
Sign-in to Mimecast can either be “service provider initiated” (where you sign-in via mimecast’s web portal), or “idenity provider initiated” (where you sign-in via Entra myapps.microsoft.com portal). But why not both! This post shows how to enable both at once.
Enabling both service provider initiated and idenity provider initiated sign-in for Mimecast
The Mimecast docs describe how to setup idenity provider initiated sign-in Mimecast docs SSO with Azure AD Premium
To enable sign-in from either MyApps portal or mimecast website, add two Entity IDs in a custom Entra ID Enterprise App as follows.
- Create a custom application in Entra ID enterprise apps and configure for single sign-on using SAML. DO NOT USE THE MIMECAST APP FROM GALLERY (though you can save the mimecast logo from gallery app for use later…)
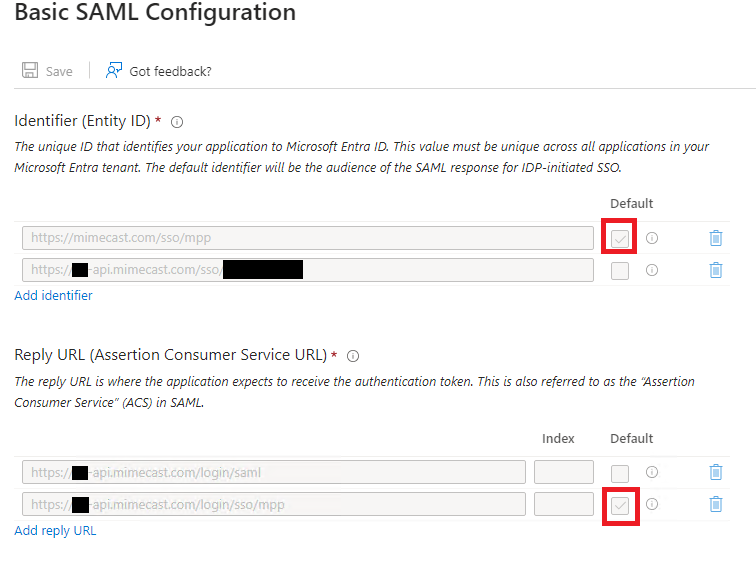
- Two Idenitifer (Entity ID) entries as follows:
- https://mimecast.com/sso/mpp (Set this as default - mpp is mimecast personal portal)
- https://xx-api.mimecast.com/sso/ACCOUNTCODE (see table one in docs for regional URL)
- Two Reply URLs as follows:
- https://xx-api.mimecast.com/login/saml (see table two Service Provider Initiated column)
- https://xx-api.mimecast.com/login/sso/mpp (Set this as default. See table two Idenity Provider Initiated column)
If you use custom app registration all other fields are optional and can be left blank. Delegate access to the app as required and test.
After login to Mimecast Personal Portal, admins can enter the URL for the Mimecast apps portal at https://regional mimecastURL/apps. Haven’t found a way to direct all users or admins to the Mimecast apps portal.
References:
